Single Sign-on: SSO
Connect SAML/ SCIM to expedite your team's onboarding process

What is Spekit?
Spekit is a B2B web application and chrome extension where users can create documents and other resources that can be referenced by anyone in their organization, on any website and through a chrome extension. A primary use case for the app is onboarding new employees.
My role
UX Researcher, UX Designer
Platform
Responsive Website
Year
Winter 2021- Spring 2022
Project Overview
We designed the process to connect SAML/ SCIM and enable SSO. We encountered an issue with pairing existing user data between Spekit and our customer’s IDP, but we built an MVP solution with plans for improvement in the next iteration.
the UX challenge
Our goal for this project was to allow customers to mass-onboard employees and allow employees to login with SSO. Our platform allows customers to create multiple accounts with the same email, making the SAML/ SCIM connection process even more complicated.
Our high level goals were to:
-
Allow connection to SAML and SCIM
-
Create a process for customers to connect existing Spekit user data to their IDP
High level definitions to know:
SSO Single Sign-on - Authentication method that allows users to login to multiple apps using one set of login credentials
SAML Security Assertion Mark-up Language - Enables you to securely access multiple web applications with one set of login credentials (allows SSO without user management)
SCIM System for Cross-domain Identity Management - Manages user identity information, users and groups (user management for SAML)
IDP - Identity provider - A system that manages SAML and/ or SCIM
the business challenge
We needed to build this feature in 2-3 months for beta testing. Leadership had received pressure from many existing customers and some new leads had gone cold primarily because we didn’t support SSO. Customers had existing user management framework using SCIM and didn’t want to invest time in rebuilding it in Spekit and managing it separately.
the process
The process for this project relied heavily on user testing and communicating with customers. SSO is a pretty standard feature. What’s unique to Spekit is the way we link Spekit and IDP accounts. It’s a technical issue that can only be solved through several rounds of improvements, where we learn from customers after every release.

Learnings + impact
personal takeaways
In this project, I was able to think creatively under strict time constraints. I worked with our devlopers to create a working MVP where we understood and minimized it’s risks. I learned the importance of working with all members of the team, including Sales, Support and Customer success.
impact
In 2 months, we deployed an MVP for enabling SSO that worked for most of our customers; users could now connect SAML and SCIM with our app. To cut some of the time, we also used a third party app, workOS, to connect Spekit to their IDP. We, then, began work on more specific user cases like connecting SAML without SCIM and improvements based on user feedback.
Research
the focus of our research
This project started with previously gathered user data from our sales and customer success teams. We knew:
-
some existing customers have built team/ user structures in their IDP and want a way to use it to manage Spekit
-
enterprise customers wouldn’t buy Spekit unless we supported SSO since they didn’t want to invest the money/ time to manage teams and 300+ users in Spekit, separately from their IDP
-
users want a way to quickly and securely login
With this in mind, we knew this was the correct solution. Our research process focused on understanding the scope and how to actually integrate this highly technical connection in a simple way.
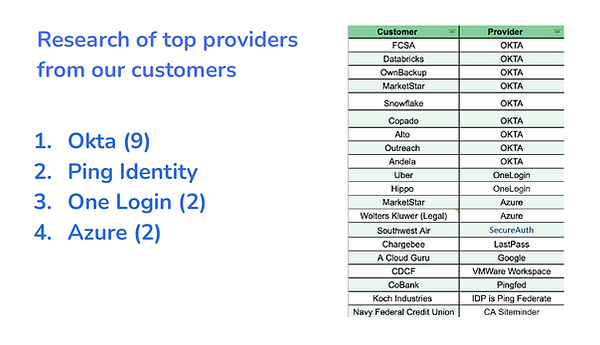
which providers to support?
Connecting SAML and SCIM is a technical process that can vary from provider to provider. We wanted to make sure we could support the majority of our customers as soon as possible so we researched which providers were most common among our largest customers (including all that requested this feature)
understanding our actual scope
Connecting SAML and SCIM is a very technical process. We weren’t entirely sure what we needed to build.
-
Should we build the connection process or use a 3rd party app?
-
If we use a 3rd party app, what do we have to build?
-
Can you manage users that were pushed from an IDP, in Spekit?
-
Would groups from an IDP be compatible with groups in Spekit?
-
Would there be overlapping user/ team data and if so, how do we clean it up?
-
We currently allow users to create multiple accounts with the same email, how would this interact with an IDP?
Planning
a spike
Our dev lead, our product manager and I needed a spike to answer some of these questions. We wanted to have an MVP to beta test in 2 months because some large customers were waiting on this to roll out.
in-house or 3rd party?
Based on our desired timeline, we decided to use workOS, a 3rd party app, to make the connection between our app and our customers’ IDP. This meant that we only needed to build the interface to start the connection and a way to identify which IDP to direct to.
what do we have to design?
The remainder of the project could be broken down into 3 parts:
-
Connect to SAML/ SCIM
-
interface to initiate SAML/ SCIM connection
-
ability to identify customer workspace
-
connection loading and success states
-
-
Connect existing accounts
-
ability to select one account to connect to IDP for emails with multiple Spekit accounts
-
-
Establish rules for user management between Spekit and IDP
-
different UI to differentiate Spekit and IDP teams and users (since they have different management requirements)
-
Connect to SAML/ SCIM
the user flow
We understood that the process to connect SAML and SCIM is fairly standard and linear, especially since we’re working with workOS. The 2 major differences for Spekit are:
-
We require a specific step to connect existing accounts to their IDP. (discussed later)
-
We won’t support connecting SCIM without SAML for our MVP. This will be extra cost and our customers haven’t shown a need for this

the overall design
We quickly put together a prototype to test.
The later part of this user flow is primarily in workOS, so most of our questions are with connecting existing user data and the unique workspace name.

validating the design
With the usability test, we wanted to explore 2 concerns.
-
We need a name to identify each organization. Is it clearer to call it a “workspace name” or “domain name” or something else? Would end users know what to input?
-
When reading the steps to connect existing users, do users respond better to numbered steps or information with bulleted tips?
We set up a series of A/B test, using usertesting.com to compare 2+ ideas for each concern.

Connect existing accounts
select one account to connect to IDP
This was a very specific problem that we needed to walk our customers through. Our customers are unfamilar with this process. They would only have to do it once, but need to do it correctly.
the technical problem
Spekit allows users to create multiple accounts with one email. However, most other apps (IDPs included) only allow one email per account. So we needed to find a way for our end users to select the account that they want to connect to their IDP.

a discussion with stakeholders
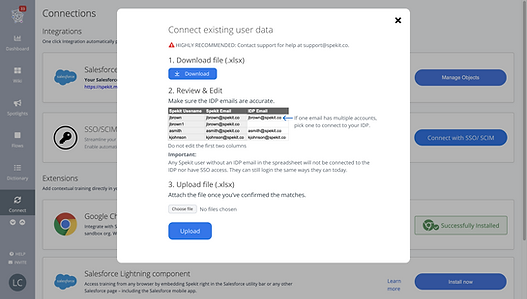
After a discussion with our stakeholders, we decided on a skinny solution (using .xlsx) with moderate risk that would eventually be replaced after our MVP was released. In the meantime, our CS team would walk our customers through the connection process.
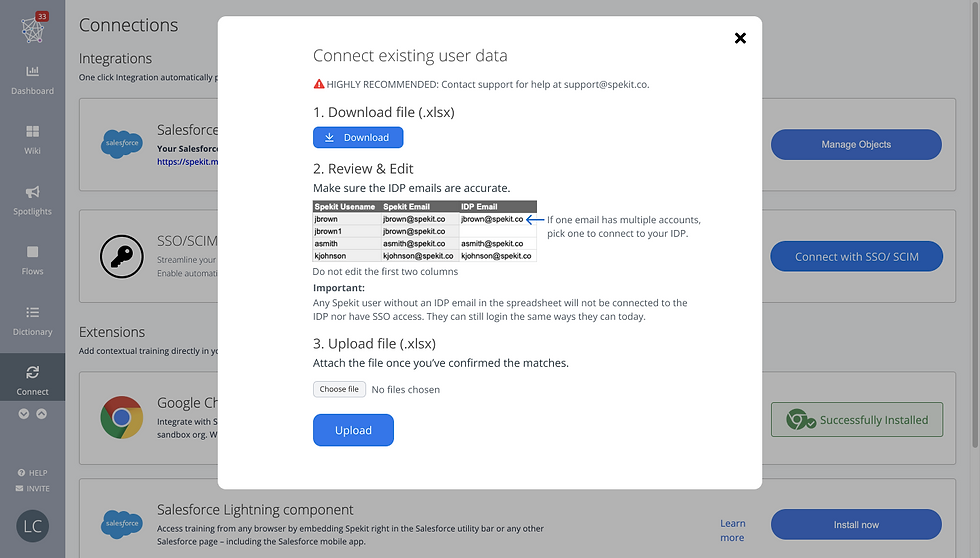
how does this work?
As a part of the SAML/ SCIM connection process, if customers have more than 2 users, they would follow these step. (New customers with fresh accounts could skip this.)
-
Download an excel file with user data, duplicate accounts would appear on top
-
Review the emails to make sure they’re correct and for accounts with multiple emails, input the email next to the account that you want to connect
-
Upload this excel sheet
what are the risks?
We didn’t want customers to scramble their user data, so the worst case scenario is that they won’t be able to proceed. The upload had strict requirements or users would receive an error message. Users might be frustrated, but at least their data was protected and they can contact our support team.
we were correct to expect risks
Although we told customers to work with their CSMs to connect SAML/ SCIM, a few customers successfully connected without our help. On the other hand, some customers had a lot of issues.
For example: The Spekit admin were oftentimes not the IT admin (IT admin managed SAML/ SCIM connections). So there would be emails between them that prolonged the connection process.
We documented these issues as improvements for after the release.
Establish rules for user management
Spekit vs IDP user management
We understood that our customers typically set up user management frameworks in their IDP that they expect to use for all of their apps, but we also understood that each customer treated their IDP differently.
-
Some used SAML and SCIM
-
Some only used it for SAML and not user management
-
Some only set up SAML to the point where SSO was enabled
-
Some expected JIT provisioning
With this in mind, we didn’t want an IDP to retire their Spekit team structure. We wanted to give our customers the flexibility of managing users in Spekit and IDP.
*Customers that only wanted their IDP teams could simply delete their Spekit teams.
establishing rules
The activation leads (1 BE dev, 1 PM, and I) met to define the specific rules for which aspects of user management would happen via IDP and which would happen in Spekit. We focused on what would work for the majority of our customers.
Essentially, any IDP data would reflect in Spekit, but Spekit data would not reflect in the IDP.
New customers that used IDP could just use their IDP for user management.
Customers that didn’t have an IDP would just Spekit for user management.

differentiate Spekit and IDP
Our initial plan was to add an icon next to anything from an IDP. It was a way to say “hey, this is from your IDP so it has special permissions.”
icons are hard to add into dropdowns
After we went into development, our FE team informed this was going to take longer than expected, like a month on it’s own. This would push us passed our expected release date, so it was back to the drawing board.
We came up with a quicker solution that wasn’t as elegant but worked for an MVP. Instead of an icon, we would add “(IDP)” to the end of all IDP teams.

Next steps
supporting our internal team
My team became the experts on SSO within our company, so we needed to educate our Support, Customer Success and Sales teams. We prepared a company wide presentation along with an FAQ doc to answer the most anticipated questions.

the launch and what we learned
Our beta program launched in Nov. 2021. In 2 weeks, we were able to connect our first customer! It went fairly smoothly, with the main problem being the process to connect existing users.
In Dec. 2021, this feature went live for all customers. In Jan. 2022, we built JIT provisioning, enabling customers with SAML to provision accounts. As more customers connect SAML/SCIM, we documented information for future improvements.
-
New customers had no issues connecting SAML/ SCIM.
-
Connecting existing customers using a .xlxs file was an issue. There were too many issues that users could encounter. -
There’s a disconnect between IT admin and Content admin. IT admin are typically the ones connecting SAML/ SCIM, but they don’t know which end users use Spekit -
Some customers switch IDPs, requiring us to disconnect their SAML/ SCIM connection -
The number of customers who want to connect SCIM without SAML is growing
next steps
In Q2 of 2022, we plan to improve how we connect existing customers with multiple accounts. We’ve planned an in-app interface where admin can select which user to connect to their IDP accounts.
-
The accounts will be grouped if they have the same email (not case-sensitive).
-
The accounts will be sorted based on when they were last active (most recently active on top)
-
The first account will be pre-selected

further in the future
We have a couple of other improvements already planned.
-
ability to disconnect SAML and/or SCIM
-
ability to connect SCIM without SAML
